Ransomware resilience: protect, detect, recover
Ransomware is no longer just an IT issue—it’s a business issue. Kaseya delivers end-to-end ransomware resilience, ensuring businesses can prevent, detect and recover from attacks—all from one integrated platform.
Get a demo
Defending against ransomware at every step
A comprehensive ransomware resilience strategy must cover every stage of an attack, from prevention to recovery. Kaseya is the only solution that provides a seamless, integrated approach to protecting businesses of all sizes from evolving threats.
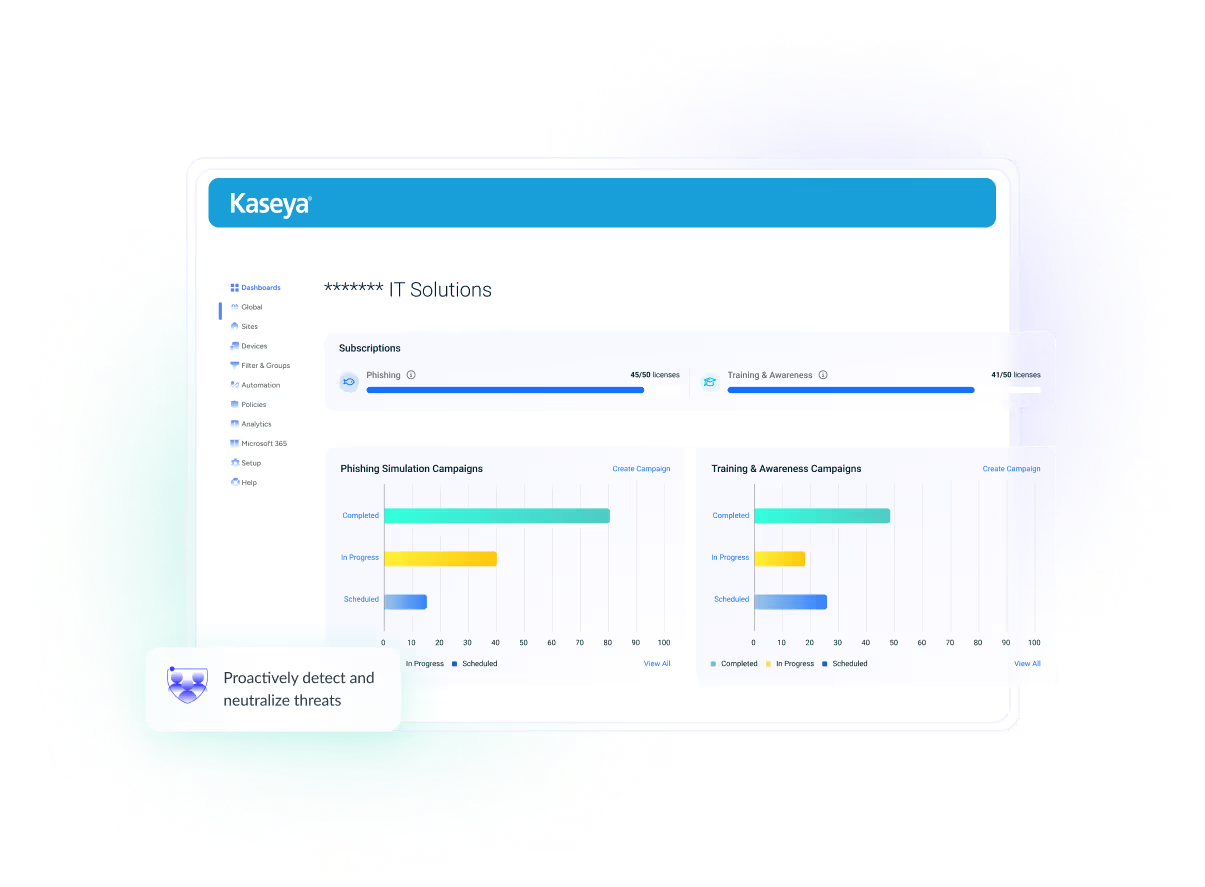
Prevent attacks before they happen with automated endpoint management
Prevention is the first step in ransomware defense. Automated endpoint management safeguards infrastructure and reduces the attack surface. Security awareness training further strengthens defenses.
“Before training, we had 77 people click a bad link, and 30 people submit personal information. After training, 11 people clicked a bad link and nobody submitted personal information."
John Masci | Systems Administrator, Canisius High School
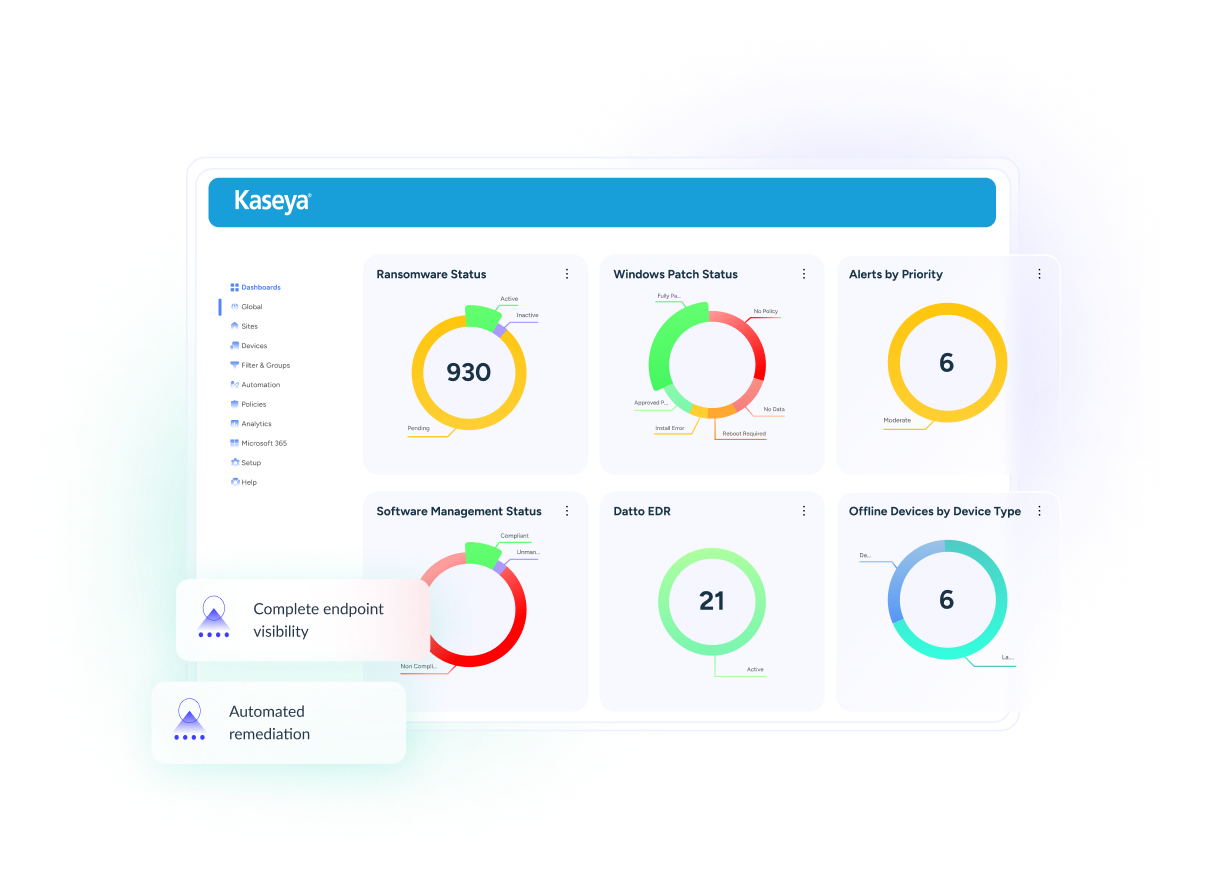
Detect threats faster with real-time monitoring and alerting
Ransomware threats are constantly evolving, making real-time detection and response essential. Kaseya leverages advanced threat detection to identify and neutralize ransomware before it spreads.
"The response time was a little over a minute from the start of the encryption that triggered the alert and the response of the ransomware policy.”
Casey Postma | Cybersecurity Lead, IT Partners+
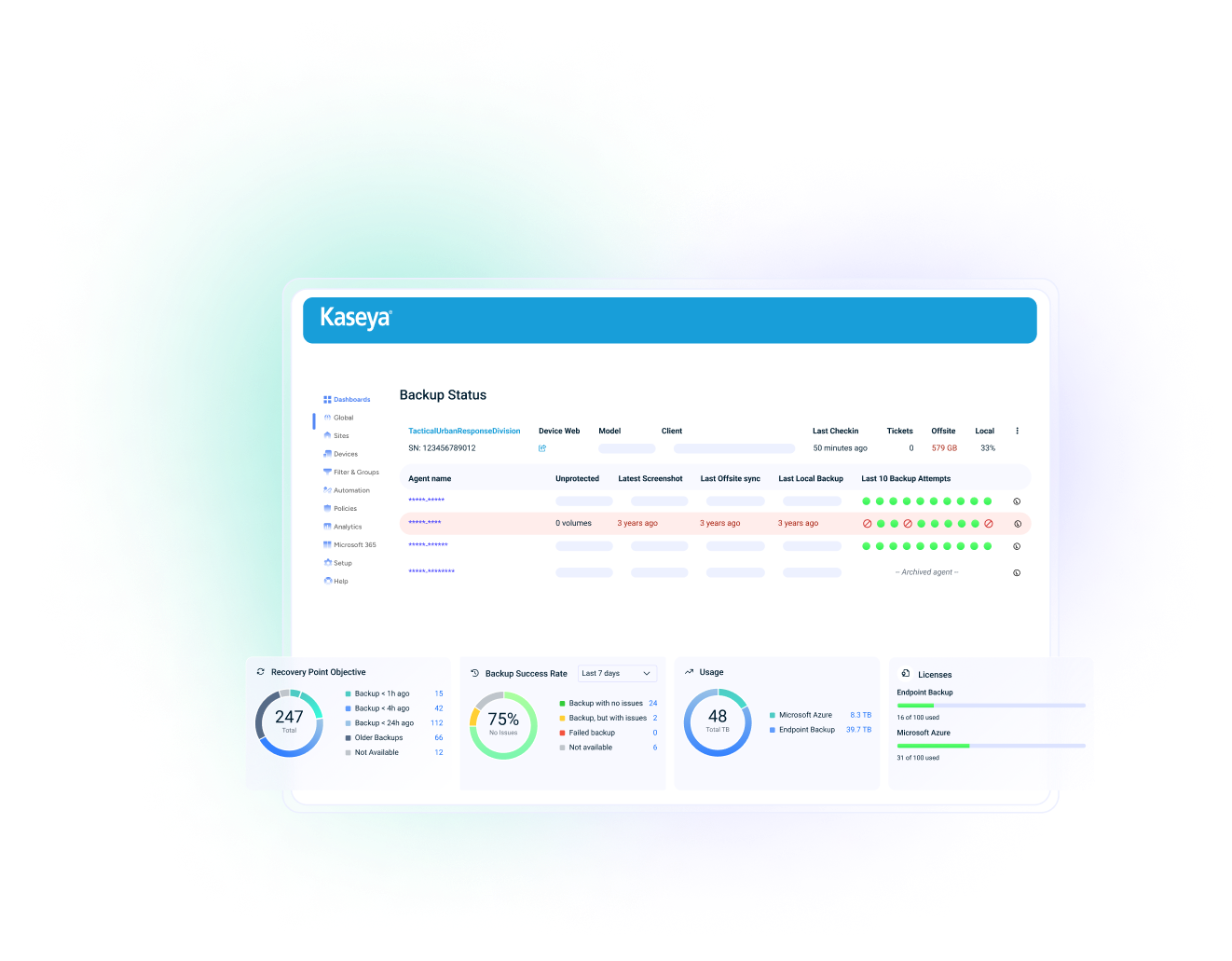
Recover easily with backups made untouchable to cyber attackers
Despite the best defenses, ransomware attacks happen. Kaseya’s backup solutions provide industry leading recovery times plus an immutable cloud to ensure data remains protected even if ransomware targets backups.
“We were able to respond, contain and eliminate the infection, and recover in a matter of minutes!”
John Little | Enterprise System Architect, Gila Regional Medical Center
Leverage a multi-layered approach to achieve ransomware resilience
Develop a vigilant workforce
Security awareness training, phishing simulations
Minimize the attack surface
Vulnerability scanning, automated patch management
Shield users from threat vectors
Anti-phishing software, DNS filtering
Facilitate secure access
Dark web monitoring for compromised credentials, secure password management
Monitor for malicious activity
RMM-based ransomware detection, endpoint detection and response, managed SOC, antivirus
Block threats from spreading
Automated quarantine of infected endpoints, termination of malicious activity, encryption blocking
Make backups invisible
Our immutable cloud makes backups untouchable to bad actors and rogue employees
Restore systems and data
Rewind like it never happened with backup solutions purpose-built for security and fast recovery
Boost your ransomware knowledge
Keep your systems secure with a range of resources designed to help you prevent, detect, and respond to ransomware threats effectively.








